Which of the Following Best Describes a Rootkit
B A desire to be helpful. Which of the following best describes a rootkit.

Figure A1 Nickle Qemu Kqemu Defeats The Adore Ng Rootkit Guest Os Download Scientific Diagram
A destructive program disguised as a real program such as a screensaver.

. A virus that changes its code as it delivers the infection. Which of the following terms best describes this software. Apply only the hotfixes that affect to software running on your systems 27.
A program that easily can hide and allow someone to take full. Software that reports data such as surfing habits and sites visited. Which of the following is also known as ZeroAccess and has virus Trojan horse and rootkit components.
A virus that changes its code as it delivers the infection. The security analyst now needs to deploy a protection solution against this type of malware. Which of the following best describes a rootkit.
The term rootkit is a compound of root the traditional name of the privileged account on Unix-likeoperating systems and t. Software that provides the originator with the venue to propagate. Which of the following best describes a vulnerability.
A destructive program disguised as a real program such as a screensaver. D A lack of fear of being caught. Software used for the collection of personal data.
Software that provides the originator with the venue to propagate. Upon investigation the. C The intent to reform.
Software used for the collection of personal data. A rootkit is a collection of computer software typically malicious designed to enable access to a computer or an area of its software that is not otherwise allowed for example to an unauthorized user and often masks its existence or the existence of other software. At which layer of the OSI model does a proxy operate.
Software hidden on a computer for the purpose of compromising the system. Software that reports data such as surfing habits and sites visited. Computer viruses worms Trojan horses and rootkits are classified as which of the following.
NEW QUESTION 181 A development team created a mobile application that contacts a companys back. Which of the following is the best recommendation for applying hotfixes to your servers. Avirus bbackdoor cweakness drootkit March 24 2021 March 24 2021 Question and Answers Question.
Question 94 of 100 Identify which of the following choices best describes the technologies used to protect systems from malicious sofware. All known rainbow tables values are tried. All possible combination of characters are tried c.
The scenario describes a remote access Trojan RAT which is a type of malware that allows attackers to take control of systems from remote locations. Which of the following best describes a rootkit. Which of the following best describes spyware.
Which of the following BEST describes the type of malware infecting this companys network. Which of the following best describes brute-force password attack. Which of the following best describes what rootkits use for stealth activity.
Which of the following is any event or action that could cause a loss of or damage to computer hardware software data information or processing capability. Which of the following BEST describes the type of malware the solution should protect against. The tool then scans the system again and compares the second scan to the clean database.
All possible dictionary words are tried. All known system hash files are tried d. Software hidden on a computer for the purpose of compromising the system.
Which of the following is the most effective method to avoid rootkit infection. A hospital has received reports from multiple patients that their PHI was stolen after completing forms on the hospitals website. The program then tracks system activity and allows an attacker to remotely gain administrator access to the computer.
Replicates itself over a network to infect computers and devices. Jerry runs a tool to scan a clean system to create a database. Media players often allow you to burn audio CDs.
A A disregard for the law. D A rootkit Show Answer The Correct Answer is- C 1. Using both network and host-based anti-virus is capable of stopping malware as long as the administrator runs weekly sca Anti-virus needs to be coupled with behavioral-based detection anti-rootkit and web traffic.
Which of the following best describes an audit daemon. The Correct Answer is- D. Which of the following best describes the term cybercrime.
The trusted utility that runs a background process whenever auditing is enabled The interface that allows the administrator to handle set up initialize and modify subsystem parameters. Which of the following terms describes a Windows operating system patch that corrects a specific problem and is released on a short-term periodic basis typically monthly. Which of the following BEST describes the type of malware used by the threat actor.
When users run the software it installs itself as a hidden program that has administrator access to various operating system components. A Physical B Network C Data Link D. A program that easily can hide and allow someone to take full control of your computer from a remote location.
ARootkit BBotnet CTrojan. A rootkit typically runs processes that are hidden. All possible combination of characters.
Never responding to the sender of an unsolicited email message.

Top 1000 Passwords Password Cracking Passwords Online Security
Rootkits How Can You Protect Yourself Against Them Ionos
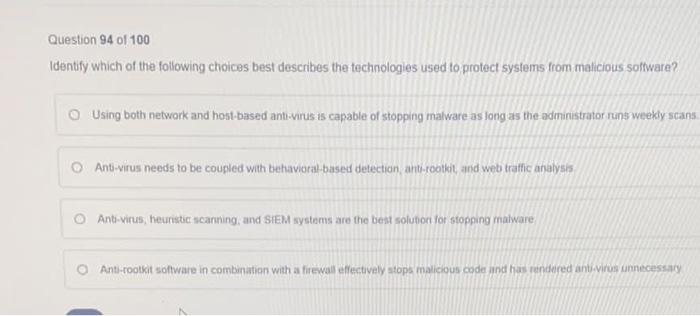
Solved Question 94 Of 100 Identify Which Of The Following Chegg Com
No comments for "Which of the Following Best Describes a Rootkit"
Post a Comment